
A Critical Layer of Protection for Your Online Presence
Ah, the internet. Remember the bygone era when the biggest online threat was accidentally clicking on a dancing baby GIF and getting Rickrolled? Those were simpler times. The internet has evolved from a simple communication platform to a complex ecosystem where businesses and individuals conduct their day-to-day activities. However, this evolution has brought about an increase in cyber threats, making DNS security a critical aspect of online protection.
DNS and its attacks
DNS, or Domain Name System, is the internet’s phonebook, translating user-friendly website names like https://secretrickroll.com (because we all know that’s totally legit) into numerical IP addresses that computers understand. It is a fundamental component of the internet, underpinning virtually every interaction.
Its simplicity and necessity make it a prime target for cybercriminals, who exploit its vulnerabilities to launch various attacks, including domain hijacking, DNS amplification attacks, DNS cache poisoning, and data exfiltration.
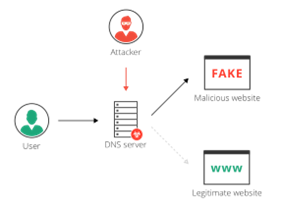
DNS hijacking
DNS hijacking is a malicious act where unauthorized individuals gain control over a domain name without the permission of the rightful owner. This can occur through various methods, including social engineering, credential-based attacks, impersonation, and cybersecurity vulnerabilities. The hijacker’s primary goal is to manipulate the registration data of the domain name, allowing them to perform illegal modifications and transfers for their benefit.

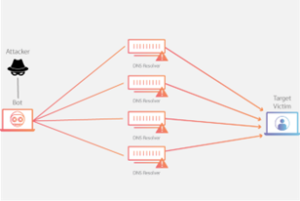
DNS amplification attacks
DNS amplification attacks involve attackers using publicly accessible open DNS servers to flood a target with DNS responses that are much larger than the original request. This is achieved by spoofing the source address of the DNS request to be the target’s address, causing the DNS server to send the response to the target instead of the original requester. The response is often much larger than the request, amplifying the volume of traffic and causing the target to become overwhelmed.
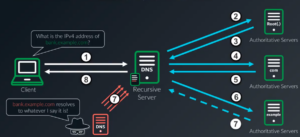
DNS cache poisoning
DNS cache poisoning, also known as DNS spoofing, exploits vulnerabilities in the DNS system by injecting false information into DNS caches, leading users to unintended or malicious websites. The attacker alters the DNS data to point to their IP address instead of the legitimate one, allowing them to intercept sensitive communications, collect private data, redirect web traffic, and potentially install malware on users’ devices.
Malware often leverages DNS for various malicious activities, such as identifying command and control points. Compromised websites can be used to distribute malware, turning devices into unwitting soldiers in a cybercriminal’s army.
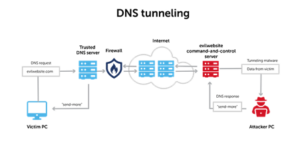
Data exfiltration or DNS tunneling
Data exfiltration or DNS tunneling is a technique used by cybercriminals to steal sensitive information from a network or IT system by exploiting the DNS protocol. This method involves embedding data within DNS packets and sending them to a domain nameserver controlled by the attacker. Since DNS traffic is generally allowed through firewalls and security systems, the malicious data in DNS packets has a high chance of leaving the organization without triggering security.
DNS Security tools
To counter these threats, various DNS security tools are available, such as Palo Alto DNS Security or Infoblox BloxOne Threat Defense. These tools offer features like DNSSEC, DNS traffic filtering, DNS threat intelligence, Domain Generation Algorithm (DGA) Detection and DNS Tunneling Detection, which help fortify your defenses and protect against a wide range of DNS-based attacks.
DNSSEC
DNSSEC (DNS Security Extensions) is a suite of IETF specifications designed to secure the DNS protocol by adding security protocols that enhance security while maintaining backward compatibility. However, DNSSEC has some problems that need to be addressed, such as the complexity of securing DNS, the large size of DNSSEC zone files, and the minimal error reporting capabilities of DNSSEC.
DNS traffic filtering
DNS traffic filtering analyzes, and controls DNS requests made on a network based on predefined policies. The purpose is to allow or block DNS queries to ensure network security and prevent access to malicious or inappropriate websites. DNS filtering can be used to block content based on categories such as hate speech, illegal activities, and malware.
DNS threat intelligence
DNS threat intelligence is the process of collecting, analyzing, and sharing information about malicious domains, IP addresses, and DNS queries associated with cyber threats. This information is specifically tailored for DNS services and contains a list of malicious domain names.
Domain generation algorithms (DGAs)
Domain generation algorithms (DGAs) are used to auto-generate domains, typically in large numbers within the context of establishing a malicious command-and-control (C2) communications channel. DGA-based malware limit the number of domains from being blocked by hiding the location of their active C2 servers within a large number of possible suspects. DGA analysis determines whether a domain is likely to have been generated by a machine, rather than a person. DNS security tools then uses these characteristics to identify and block previously unknown DGA-based threats in real-time.
DNS tunneling
DNS tunneling can be used by attackers to encode data of non-DNS programs and protocols within DNS queries and responses. This provides attackers with an open back channel with which they can transfer files or remotely access the system. DNS tunnel detection uses machine learning to analyze the behavioral qualities of DNS queries, this allows you to quickly detect C2 or data theft hidden in DNS tunnels and to automatically block it.
Choosing the right DNS security tool
Infoblox’ BloxOne Threat Defense
Infoblox offers a product called BloxOne Threat Defense, which is a cloud-based threat defense platform designed to protect networks from various types of cyber threats.
This platform leverages advanced threat intelligence and machine learning algorithms to detect and block malicious traffic in real-time, ensuring the security and integrity of an organization’s network infrastructure. BloxOne offers a robust feature set and extensive customization options, making it ideal for complex networks seeking granular control.
This solution effectively shields against a wide range of DNS DDoS attacks, ensuring continuous service uptime. It minimizes disruptions caused by attacks, emphasizing the critical importance of DNS security in maintaining business continuity. Infoblox’s solution is designed to secure organizations from DNS-based threats, providing robust protection and enhancing security posture.
In addition, BloxOne Threat Defense, Infoblox also provides SOC Insights, a groundbreaking AI-driven security capability integrated into Infoblox’s DNS Detection and Response (DNSDR) solution. One of the standout features of SOC Insights is its ability to mitigate alert fatigue by consolidating hundreds of thousands of DNS security alerts into a dramatically smaller, more manageable set of insights.
By applying AI-driven analytics to DNS activity, asset information, DNS threat intelligence, and security events, SOC Insights correlates those events, prioritizes them based on many factors beyond typical malware risk rankings, and provides recommendations for swift resolution. This not only accelerates threat detection and response but also alleviates the strain on overburdened SOC analysts.
Palo Alto DNS Security
Palo Alto DNS Security is a popular choice for businesses seeking a platform approach to cybersecurity, ensuring a comprehensive defense against a wide range of cyber threats. The platform approach enables centralized management and monitoring, making it easier for security teams to manage and respond to security incidents.
Palo Alto DNS Security prioritizes ease of use and straightforward security, making it perfect for smaller networks and businesses seeking a no-fuss approach.
From the start of May 2024 Palo Alto Introduced Advanced DNS Security. Advanced DNS Security can detect and categorize hijacked and misconfigured domains in real-time by operating cloud-based detection engines, which provide DNS health support by analyzing DNS responses using ML-based analytics to detect malicious activity. Because these detectors are in the cloud, you can access a wide array of detection mechanisms that are updated and deployed automatically without requiring the user to download update packages when changes to detectors are made. Upon initial release, Advanced DNS Security supports two analysis engines: DNS Misconfiguration Domains and Hijacking Domains.
DNS plays a pivotal role as the first traffic in a network connection, so DNS security is not a luxury but a necessity in today’s digital landscape. Investing in a robust DNS security tool is crucial for businesses and individuals alike, as it provides a critical layer of protection against various DNS-based attacks. However, it’s equally important to complement these tools with a comprehensive cybersecurity strategy that includes multiple layers of defense to ensure robust protection against evolving threats. Remember, a little internet security goes a long way, and who knows, you might even discover some genuine dancing baby videos along the way, just watch out for those sneaky Rickrolls!
TL; DR Summary of Advanced DNS Protection
The internet is a treacherous landscape where hackers exploit DNS vulnerabilities to steal data or manipulate websites you frequent. To safeguard against these threats, it is crucial to employ specialized tools for DNS security. Various options exist, each catering to different needs, with some being more user-friendly than others. Regardless of the choice, having robust DNS security is imperative in today’s increasingly perilous online environment.
DNS security plays a pivotal role in shielding against cyber threats that exploit DNS weaknesses like hijacking, amplification attacks, cache poisoning, and data exfiltration.
Solutions like Infoblox BloxOne Threat Defense and Palo Alto Advanced DNS Security offer comprehensive defenses, incorporating features such as threat intelligence, machine learning, and real-time identification of malicious DNS activities. They also go a step further by leveraging cloud-based engines to detect hijacked and misconfigured domains, thereby fortifying network security and ensuring business continuity.


