Gigamon Visibility Fabric is no longer a novelty in the world of network traffic aggregation and replication with intelligent distribution, instead it is considered an industry-leading innovative and complete traffic visibility solution. Intelligent traffic distribution is provided by packet optimization functions which make sure that specific security solutions, i.e. traffic consumers, receive only the traffic intended for them. For example, email security solutions shouldn’t be exposed to YouTube or Facebook traffic.
This approach imposes many different questions:
- What percentage of traffic is diverted to your security solutions, while not being intended for them?
- What percentage of this traffic is generated by video/Facebook/Windows Update services?
- How extensive is the processor and bandwidth load generated by these solutions?
- Can we optimize it?
Sure, we can!
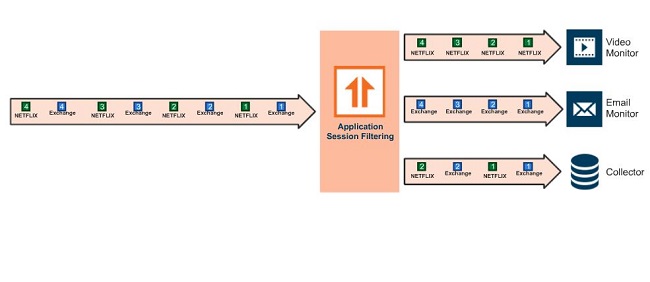
GigaSMART Application Session Filtering
ASF searches for and filters packages down to the application layer based on a selected sample and can redirect a complete session to a specific security solution even when the package containing the set sample was not the initial session package. This functionality is achieved by storing a maximum of 20 packets in a buffer – this number was proved sufficient since the required sample always appears in the first few packets of a specific session.
Traffic filtering
Not so long ago the process of determining the used protocol was very straightforward – all that was needed was to observe the necessary port and send specific traffic for inspection or simply discard it. Creation of Facebook, YouTube, Netflix and other services generating large volumes of traffic, primarily video data, meant that monitoring tools and security solutions were being crowded with irrelevant and undesirable traffic. Gigamon Application Session Filtering (ASF) solution reduces the workload of these tools, thus achieving significant savings.
Example: YouTube traffic filtering
All network traffic originating from SPAN or TAP ports is sent to port 1 which is set to network mode.
Monitoring tool or a specific security solution for inspecting web traffic is setup behind port 5 which is set to tool mode.
ASF functionality is enabled by creating the GigaSMART group. Since we want to avoid directing all network traffic to the GigaSMART group virtual port, we must create a map for directing network traffic from ports 80 and 443 to that port. Furthermore, we’ll create another map inside the GigaSMART group for filtering traffic via regular expressions and package inspection, and then create a rule for discarding this egress traffic. Additional map will be created to send the rest of the traffic to the collector passing it to port 5.
Example of regular expressions for filtering YouTube traffic:
(config map alias youtube_filter) # gsrule add drop pmatch protocol tcp pos 1 RegEx “youtube|ytimg|yt3.ggpht|tubeMogul|tmogulyoutu” 0..1000 (config map alias youtube_filter) # gsrule add drop pmatch protocol tcp pos 1 string “Content-Type: video” 0..1000 (config map alias youtube_filter) # gsrule add drop pmatch protocol tcp pos 1 string “octet-stream” 0..1750
Application Session Filtering Cookbook can be accessed here.


