
Attackers are targeting user identities with increasingly sophisticated phishing techniques, as compromised credentials make it far easier to infiltrate and thwart organization IT defenses. Relying only on passwords to protect identities is now almost an invitation for cyber criminals: 82% of breaches are involving either use of stolen credentials and phishing (according to Verizon’s Data Breach Investigation Report for 2022). The SANS Institute Security Awareness Report warns that human risk remains the biggest threat, with employees becoming the primary attack vector for cyber-attackers around the world.
Strengthening authentication with additional factors (i.e. multifactor authentication or MFA) is therefore an essential practice for all entry points into an organization: from VPN, over email, file sharing to business applications covering financial accounting, CRM, etc. Typically, the easiest way to implement MFA is by using a smartphone app that acts as 2nd factor authenticator where the user approves the authentication via a smartphone push notification (an out-of-band authentication). From Google authenticator to Microsoft authenticator, we’re all used to these smartphone assisted out-of-band methods now.
However, attackers are now catching up: using clever Attacker-in-the-middle (AitM) proxy techniques and prompt bombing, it’s now becoming routine to bypass out-of-band MFA. Actual phishing attacks against companies such as Uber, Twilio, Mailchimp, Cloudflare, and many more confirm the new techniques are widely deployed. Due to these relatively recent developments, it’s no wonder organizations such as the US Cybersecurity and Infrastructure Security Agency (CISA) now urge all organizations to implement phishing-resistant MFA to protect against phishing.
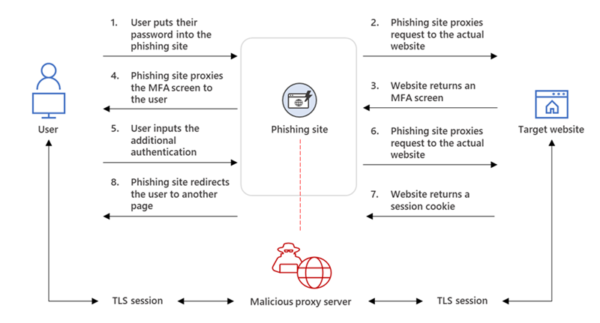
The attackers are effectively exploiting two key weaknesses with out-of-band authentication such as mobile push MFA (Multi-factor authentication)
- Is the user signing in to the legitimate website? Users are tricked into accessing a phished page that presents the same look-and-feel as the original one (for ex. 0ffice.com instead of office.com). The mobile push authenticator is by definition unaware whether the user is accessing the site via a credential stealing AitM proxy. If the user also doesn’t notice this and approves the push auth request, credentials and access tokens will be stolen.
- Is the user really triggering the push notification? Users can be triggered to approve a push auth request even if they’re not accessing the resource or are not near the device requesting access. This is typically exploiting user fatigue by sending many auth prompts until the user accepts by error or out of frustration (prompt bombing). Physical presence to the device is not checked.
Phishing resistant MFA (Multi-factor authentication) addresses the issues above by moving authentication to the same device where user is signing in (away from out-of-band such as smartphone push). In practice, this means either an authenticator integrated in the device (a Windows laptop) or a separate token (connected to the device via USB or NFC/Bluetooth).
There are two MFA (Multi-factor authentication) methods considered phishing resistant
- FIDO2/Webauthn token – supported now by all major platforms (Windows, Google, Apple) and integrated in all major browsers, making it suitable for mobile and laptop scenarios, plus special attention given to anti-phishing (see below).
- PKI token – the traditional public key cryptography offers strong authentication, but often implies client software that makes it costly to maintain in an organization context, and also has poor support for mobile scenarios. However, PKI is essential for digital signing and content encryption (e-mail, files, etc.).
FIDO2 tokens have 2 distinct properties which make them phishing resistant:
- The authenticator automatically checks if it “talks” to the assigned application/website and will not authenticate against a fraudulent website (for ex. office.com vs 0ffice.com).
- Besides the PIN, physical presence is checked via a “gesture” for ex. touching the device or a biometric check (fingerprint, face recognition, etc.), before unlocking the authenticator.
Additionally, the FIDO2/Webauthn standard brings all the benefits of PKI such as strong authentication based on public key cryptography, but with a reduced administrative overhead and a broader end-user device support. As with PKI, the user key or credential never leaves the authenticator and is not stored in the application or identity service. Contrast that with traditional credentials such as password hashes, which must be stored on the server side.
Want to test the latest FIDO2 technology? Contact us!
