
The Palo Alto Networks Security Lifecycle Review (SLR) is an online tool that summarizes the security risks faced by an organization. We all know visibility is key to prevent breaches and SLR enables precisely that: unmatched situational awareness and visibility into network traffic, provided by PANW next generation firewall solution.
Getting deep visibility usually requires in-line proxy technology, but with PANW App-ID and other built-in intelligence the whole process is much more straightforward and can provide insights even without resorting to full SSL interception and proxying traffic. PANW determines what an application is irrespective of port, protocol, encryption (TLS or SSL) or any other evasive tactic used by the application. That’s why you can do SLRs non-invasively and still gather useful insights and even discover unknown risks which the current firewall solution might be missing (such as a bot infected client).
SLR relies on the so called Statsdump file, which is an XML generated directly from the NGFWs containing summarized results of device logs. This XML is uploaded on the partner portal to easily generate white-labeled reports, as a basis for follow-up customer discussion.
Multiple options for Palo Alto Networks SLR
The typical and most basic SLR deployment will use TAP mode interfaces, where the firewall can be connected to a core switch’s span port to identify applications running on the network. This option requires no changes to the existing network design. Of course, in this mode the firewall cannot block any traffic (just like IDS) but the upside is a simple implementation.
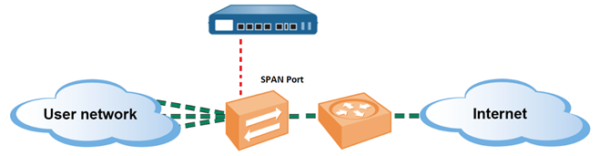
- Directly connected to L2 device on SPAN port
- IDS
- Cannot do Routing or Switching
- Cannot block traffic
- Supports App-ID, Content-ID
In situations where the core switch either can’t handle SPAN/Mirroring or TAP due to performance or any other issues, the firewall offers bridge functionality called virtual wire interface (VWire) where it’s placed inline, and the traffic passes right through it (a bump in the wire).
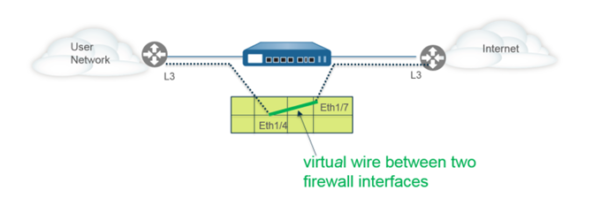
- No IP or MAC address
- Directly connected to L2 or L3 device
- Cannot do Routing or Switching
- Can do NAT and Security Rules
- Supports App-ID, User-ID, Content-ID, Decryption, DoS protection and more
Another deployment option for SLR is to use the Layer 2 interface type. Here, the firewall acts as a switch in a layer 2 network (not at the edge of the network). The Layer 2 hosts are usually geographically close to each other and belong to a single broadcast domain. Additionally, further segmenting via VLAN subinterfaces is supported.
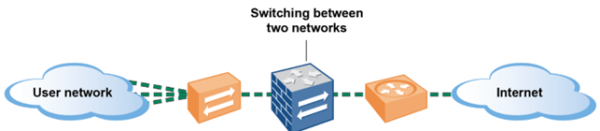
- Used when no Routing is needed
- Switching possible
- Supports App-ID, User-ID, Content-ID, etc
- Can do active actions on traffic
- Does not participate in Spanning Tree
- Forwards STP
- Supports Layer 3 VLAN interfaces
Finally, the Layer 3 interface deployment is the full routing mode with all features enabled (Including DoS prevention, VPN Tunnels, etc.). This will be rarely used for non-invasive SLR deployments and is the most common deployment mode in production.
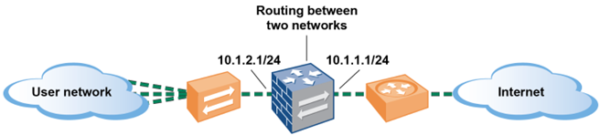
- Most used deployment mode
- NAT, QoS, IPSec, DoS protection
- Has Routing tables, Virtual Routers
- Can act as DHCP client or Server
- Supports Routing protocols
- Supports App-ID, User-ID, Content-ID
- Supports Decryption
Need help on choosing the right model and deployment mode for SLR? Want our engineer support during SLR preparation and follow-up? We’re here to help! Contact us!
