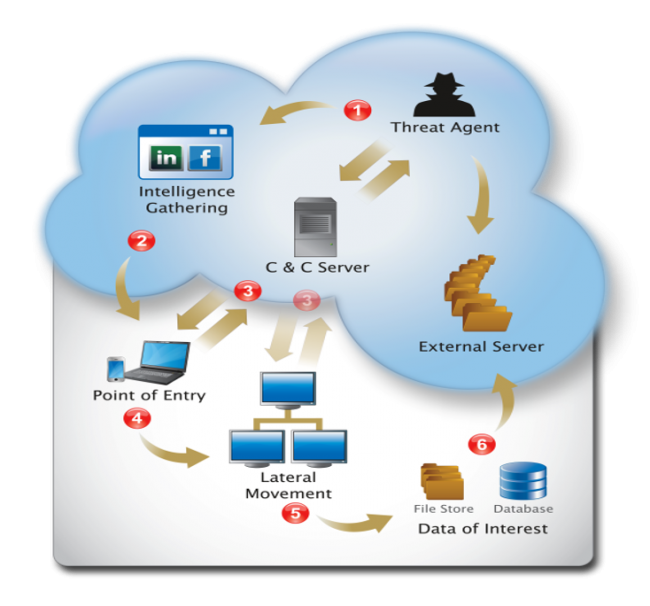
To discover insider and outside malicious actors and advanced persistent threats within networks, organizations usually invest lots of resources into sophisticated and expensive security information and event management (SIEM) solutions. These are not only complicated to install but also require trained expert staff, making the whole project a nightmare in terms of TCO.
Malicious activity is usually spread across hundreds of log line produced by various systems. For ex. the first foothold into an organization might be a phishing email prompting the user to reveal their credentials to the attacker. A second step is usually the deployment of malicious software via email attachment or drive-by download, and finally phone-home, lateral movement and exfiltration activity related to the previous steps can be seen. But making sense of the sequence of events (and the affected hosts) just by looking at logs is time consuming to say the least and requires expert eyes. Yes, there are solutions on the market to make this task easier, but the implementation effort and associated costs to run can be really high.
Wouldn’t it be easier to have simple network sensors powered by the world’s leading threat intelligence AND security event correlation done automatically for you, at a fraction of a cost? Take a look at the video below to see what Deep Discovery Director can do when joined with Inspector/Analyzer components.
In the video you can see how the Inspector component generates potentially huge amounts of network logs (as the attack is multipronged), while the Director component can condense those logs into just a few critical and meaningful events.
Of course, you can always plug the logs into your SIEM solution, but with Director it’s much easier and cost effective getting from data to event correlation.

