SSL is a set of cryptographic protocols that protect data during transmission. Although nearly ten years ago SSL was used almost exclusively by financial institutions and various login sites, SSL/TLS is obviously becoming a standard in IP communications and it use is on the rise. TLS is a successor to SSL with different versions of these protocols used when browsing the Internet, sending or receiving emails, using instant messaging (Facebook, WhatsApp, Viber), making VOIP calls, and so on.

Why is there an increase in the amount of encrypted traffic?
Some of the reasons are:
- Desire for privacy,
- Growth of social networks,
- Accelerated transition of websites to HTTPS triggered by the latest changes in browser behavior
- Compliance with regulations,
- Availability,
- Using web-based applications,
- Introduction of new standards – HTTP/2, TL 1.3.
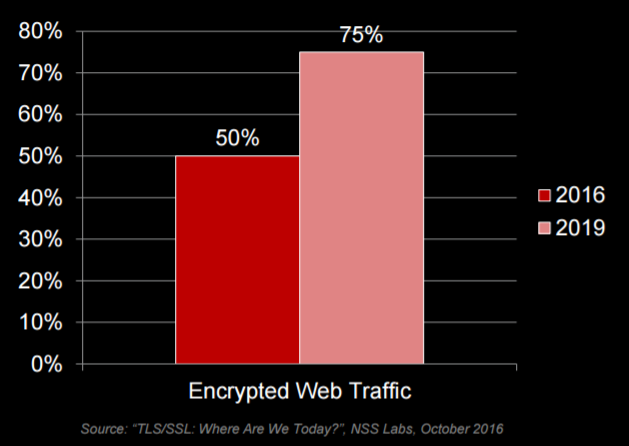
HTTPS was created by combining HTTP and SSL/TLS protocols. This resulting protocol provides verification of visited websites, privacy protection and preservation of integrity of data that is being exchanged. Most websites are expected to use HTTPS in the coming years – according to Google Chrome Web Browser statistics, over 50% of websites are currently displayed using the HTTPS protocol, while users spend 2/3 of their total surfing time visiting these secure sites.
Although SSL provides data privacy and secure communications, it also introduces new challenges to the networking environment because it hinders or disables verification of encrypted traffic. Because of this, encrypted communications pass through the network without any verification and become, at least from a security standpoint, its weak spot. This poses a high level of risk to businesses because malicious users can easily inject malicious software into their networks within such encrypted traffic. Research shows that between 50% and 75% of attacks are hidden within encrypted traffic. Insight into encrypted traffic passing through today’s networks became a real business necessity.
Given that encrypted traffic processing has a significant impact on the performance of network devices, even when decryption is natively supported (especially challenging when using new 2048-bit certificates), choosing appropriate solutions should always be a priority.
F5 SSL Everywhere
F5 SSL Everywhere architecture is based on a custom-built SSL stack that is part of each F5 LTM implementation. Although customers can choose between two SSL stacks; COMPACT, based on the OpenSSL library, and NATIVE stack that is part of F5 TMM (Traffic Management Microkernel) system, F5 recommends choosing the NATIVE stack which is an optimized SSL stack with the ability of using hardware acceleration for most SSL algorithms.
Users encounter different situations on a daily basis where it is possible to utilize advanced SSL traffic processing capabilities by using F5 technology. As strategic control points inside the network, F5 devices provide a unique insight into encrypted traffic. What differentiates F5 from other vendors can simply be explained in several key points:
- Flexible implementation method that ensures simple integration even in the most complex network application environments and centralization of SSL/TLS decryption and encryption,
- Simple integration of latest cryptographic technologies without the need for demanding and expensive architectural upgrades,
- Leading vendor in the decryption and encryption product segment that offers the ability to offload decryption functions from background servers to ensure they operate as intended – delivering applications to end users,
- Dynamic service chaining compares URLs and traffic according to set security policies that define whether the encrypted traffic can pass through the network uninterrupted or should be decrypted and sent for further analysis,
- Support for advanced cryptographic algorithms,
- Two-way SSL/TLS decryption and encryption using HTTP/2 and the latest SSL/TLS protocols with the implementation of PFS functionality.
Insight into inbound SSL traffic (publishing public web services): Flexibility of Implementation
For the longest time role of an ADC device from a SSL aspect was to monitor traffic in the inbound direction, which means that ADC devices were used to decrypt SSL traffic. Re-encrypting client-to-server traffic was almost exclusively used by financial organizations. Today, inbound scenarios include advanced functions such as importing PKCS12 keys, rapid implementation of new cryptographic algorithms, and adapting new cryptographic algorithms.
Most commonly used SSL/TLS protocol application is securing user access to Internet applications located in the data center. Organizations use ADC devices to perform “SSL bridging” which means that the ADC device, in this case F5 LTM, will decrypt inbound traffic, take action in accordance with set configuration, then re-encrypt the traffic and send it to the destination server located in the data center. Decrypting traffic on the ADC device allows you to take various actions; additional traffic optimization and manipulation options, but also provides L7 traffic inspection and protection against various attacks attempting to enter the network within encrypted traffic. It is also important to note that this ensures compliance with various regulations, such as PCI-DSS, especially in the financial sector.
Certain number of F5 users use F5 devices to deliver applications over SSL which only require traffic forwarding and L4 load balancing. In this case, millions of connections pass through F5 devices, however F5 devices do not terminate nor check these connections. They only provide a certain level of SSL data flow control. This implementation method does not provide the ability to inspect L7 traffic, but allows you to use different optimization options on a TCP level. This implementation method is called SSL pass-through.
Managing private keys
Private SSL keys are one of the most valuable possessions of any organization. Any attacker who succeeds in obtaining a private key can easily create a completely identical application and a perfect phishing portal. Due to this, organizations are very serious about keeping their private keys private and secure. Many security architectures are designed to keep private SSL keys deep within the data center, far from network perimeter. F5 devices process most SSL traffic inside the data center which very often contains dozens of private keys.
Financial organizations often require integrating the F5 system with existing HSM systems. F5 products can be integrated with external HSM devices since 2000. HSM devices are developed specifically for environments that require high level of security where private keys cannot be compromised. Performance of such devices was never a priority. As most businesses began migrating to the Internet environment over time, demand for these devices started increasing. When decoding SSL traffic became a functionality of ADC devices, organizations discovered they could achieve significant financial savings since HSM devices come with a pretty high price tag. Likewise, modern HSM devices are actually network devices which provide administrators with a central place for managing private keys, while organizations have the option to purchase a smaller number of HSM devices.
F5 Networks is a leading vendor, following and creating all the latest IT trends. In today’s world, with more and more talk of outbound SSL visibility and shifting market focus to technologies and vendors that can provide such solutions, F5 follows this trend and enables its customers with ways to ensure outbound SSL visibility.
Visit us again soon and find out more about the solutions that F5 delivers in the outbound SSL visibility segment!




