
Are you a system integrator seeking better ways to manage customers’ network infrastructure and security?
Network security is crucial: SMB organizations of all sizes have a network infrastructure that needs to be managed and secured. There are a multitude of different users and devices (from laptops to IoT devices) that connect to the network, plus copious amounts of data, that all need to be protected.
Integrate and see the benefits
Typically, wired networking, wireless access, firewall security and endpoint security are separate silos that need dedicated attention and management. This increased complexity can easily lead to security issues. Converging both networking and security does not only provide benefits in reduced infrastructure and management costs, but it also provides better opportunities to utilize data from one silo and use it for policy enforcement in another one.
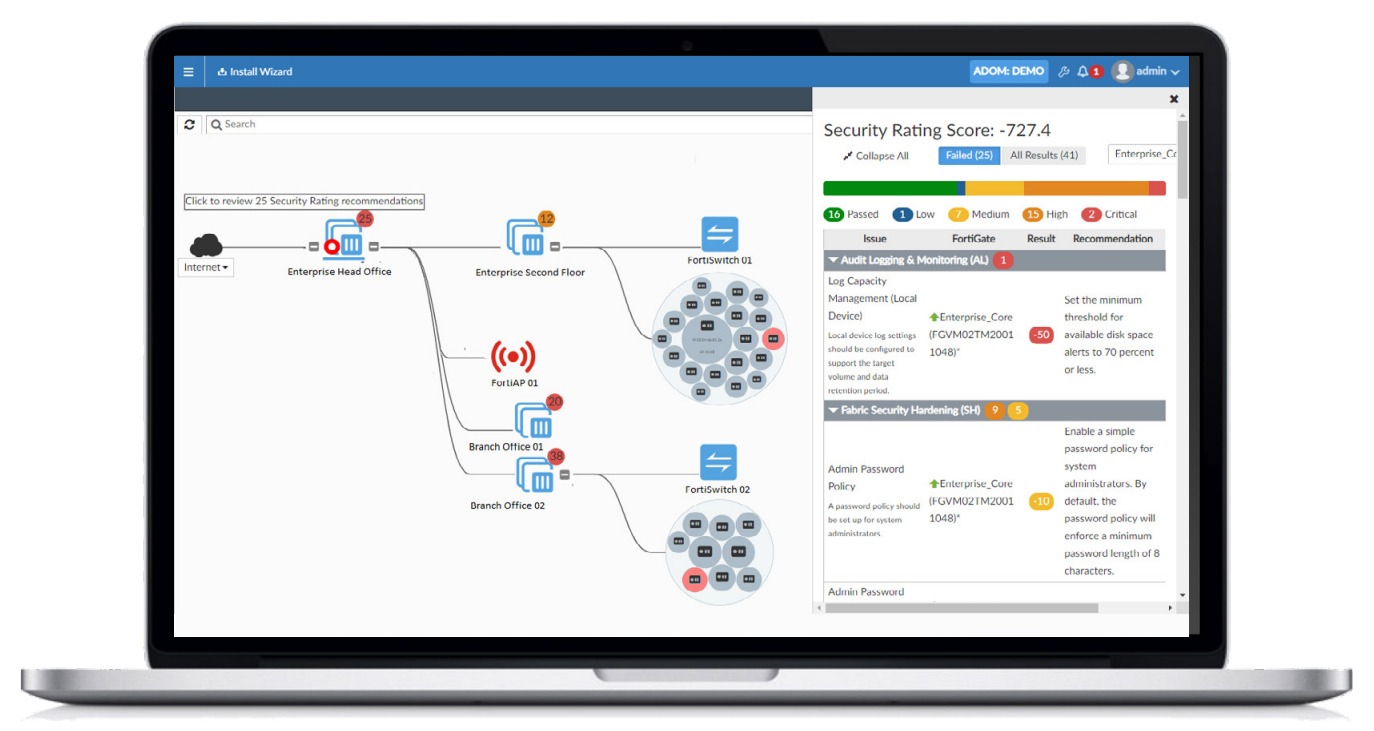
For example, let’s suppose a customer’s office has some network switches and WI-FI access points. In the case of a FortiSwitch fully integrated with FortiGate, the switch ports inherit the same properties as the firewall, making them extensions of the firewall. The same principle goes for the FortiAP WiFi access point.
Refined network security
This so-called Security Fabric integration enables cross-product functionality that can further allow automation when facing a threat. When an infected client is detected through bot traffic detection, the switch or AP can block the device until the problem is remediated.
For office locations, this LAN and firewall integration can be further enhanced with built-in Network Access Control (NAC). While basic NAC services are needed in almost any network, NAC has traditionally been a costly add-on for most companies.
Fortinet offers NAC services built into the system. It constantly monitors the network for all IP-connected assets and can automatically assign network based on device type, manufacturer, operating system, and so on. This in turn can be used to refine network security policies on the FortiGate firewall. For example, automatically reduce network access for unmanaged IoT devices and prioritize internet access for fully managed company laptops.
Further intelligence and enrichment can be obtained by integrating endpoint security (usually a separate and non-integrated aspect of security). FortiClients can add much more metadata for the firewall to make policy decisions. These include the logged-in username, the software used, whether antimalware is used, patch level, operating system, etc. These security tags can instrument the firewall to react (for example, deny access to non-compliant devices, enforcing the principle of Zero Trust (ZTNA)).
With a common security operating system, FortiOS, and a single source of threat intelligence, FortiGuard, the converged networking and security solution from Fortinet eliminates both the complexity and the protection shortcomings that occur when mixing different security and networking vendors. Enabling the entire ecosystem to behave as a single entity from a policy and logging perspective reduces the risk from advanced threats. This differs from the majority of network access vendors that require additional software and management consoles to achieve such integration, increasing complexity and cost, often through recurring fees.
Simplify and manage from anywhere with SaaS
Smart system integrators have already figured it out: it used to be that cloud and SaaS were associated with increased risks and less security. However, the global explosion of cyberattacks has made it clear that breaches are often the result of IT complexity and insufficient time for proper maintenance. Reality shows that overburdened IT teams are being overrun by threat actors, leading to ransomware and other damaging attacks.
After seeing so many breaches, the Cybersecurity & Infrastructure Security (CISA) in its Cyber Guidance for SMBs clearly states what used to be controversial is now becoming conventional wisdom:
One major improvement you can make is to eliminate all services that are hosted in your offices. We call these services “on premises” or “on-prem” services. Examples of on-prem services are mail and file storage in your office space. These systems require a great deal of skill to secure. They also require time to patch, to monitor, and to respond to potential security events. Few small businesses have the time and expertise to keep them secure. […] The solution is to migrate those services to secure cloud versions […]. These services are built and maintained using world-class engineering and security talent at an attractive price point. We urge all businesses with on-prem systems to migrate to secure cloud-based alternatives as soon as possible.
What goes for e-mail and file sharing (as per CISA advice), also applies to network and infrastructure management. Moving to SaaS makes sense from a management and security point of view. Managing your customers remotely without opening individual public facing VPN tunnels that need attention, can increase both productivity and security.
Complete MSP management solution
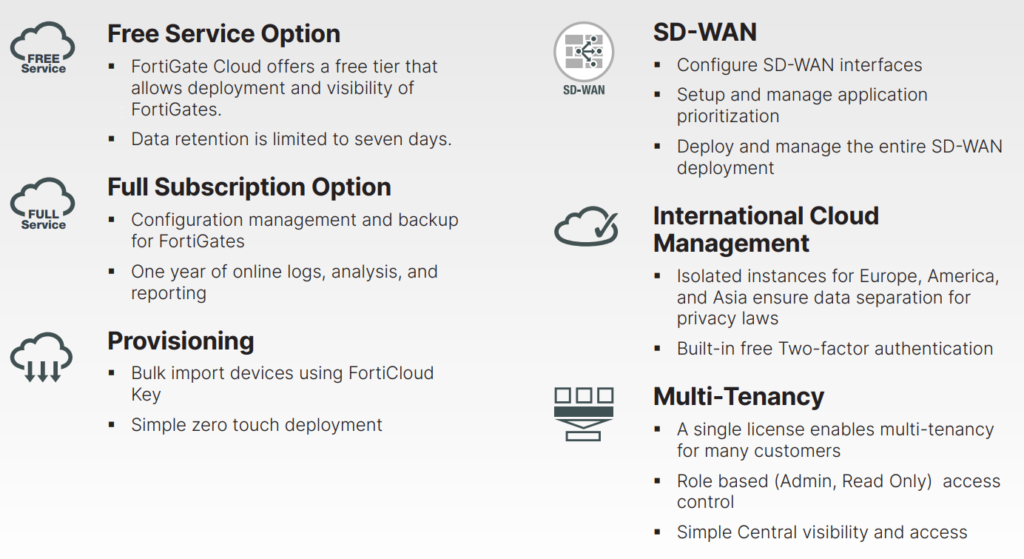
FortiGate Cloud is a cloud-based SaaS, offering a range of management and services for Fortinet FortiGate firewalls. FortiGate Cloud offers zero touch deployment, configuration management, reporting, and analytics.
FortiGate Cloud can grow with your requirements from a single FortiGate to a complete MSP management solution for thousands of devices across multiple customers. All FortiGates include FortiGate Cloud registration functionality in their firmware that allows an individual or multiple devices to provision themselves with minimal on-site expertise.
The SaaS model eliminates the need for upfront capital purchases and simplifies management, maintaining a single pane of glass for overseeing security and networking infrastructure. FortiGate Cloud provides control over FortiGates while providing granular visibility and reporting at the same time. Role-based access control provides flexibility in managing users and Multitenancy enables the management of customers, and users with simplicity and ease.
Interested in more info? See why partnering with Exclusive Networks and Fortinet makes sense!

