Making a Mesh of Things
The Cybersecurity Mesh Architecture Approach
Sign up to the Dedicated Cybersecurity Programme
What is the Cybersecurity Mesh?
The Cybersecurity mesh is a flexible, composable architecture that integrates widely distributed and disparate security services. Cybersecurity mesh enables best-of-breed, stand-alone security solutions to work together to improve overall security while moving control points closer to the assets they’re designed to protect. It can quickly and reliably verify identity, context and policy adherence across cloud and non-cloud environments.
The cybersecurity mesh is a modern conceptual approach to security architecture that enables the distributed enterprise to deploy and integrate security to assets, whether they’re on premises, in data centers or in the cloud.
90%
Gartner predicts that by 2024, organizations adopting a cybersecurity mesh architecture will reduce the financial impact of individual security incidents by an average of 90%!!
The Cybersecurity Mesh is ‘bang on’ trend
This year Gartner listed the Cybersecurity Mesh architecture as one of their top cybersecurity trends for 2022.
Why? Because interoperability – the ability for technologies to communicate and share information – has become an enormous problem within the cybersecurity industry.
Technology manufacturers have historically worked in silos, with the aim of create best-of-breed solutions for businesses to procure. And they’ve been largely successful in doing so, meaning that businesses have lapped up these technologies.
The result? Businesses with a highly complex cybersecurity architecture, with some CISOs reporting that their portfolios contain a staggering 46 or more technologies!!1
Cybersecurity relies upon visibility, but as portfolios grow, visibility declines. Often under-resourced security teams are left having to gather data and information across disparate systems, and it is this interoperability issue that means breaches are not being identified for up to 287 days2.
The Solution? A cybersecurity mesh architecture. This open approach to cybersecurity will reduce complexity whilst improving efficiency, ultimately leading to a better overall security posture.
Learn more about the solutions that comprise the Cybersecurity Mesh
Explore the Cybersecurity Mesh
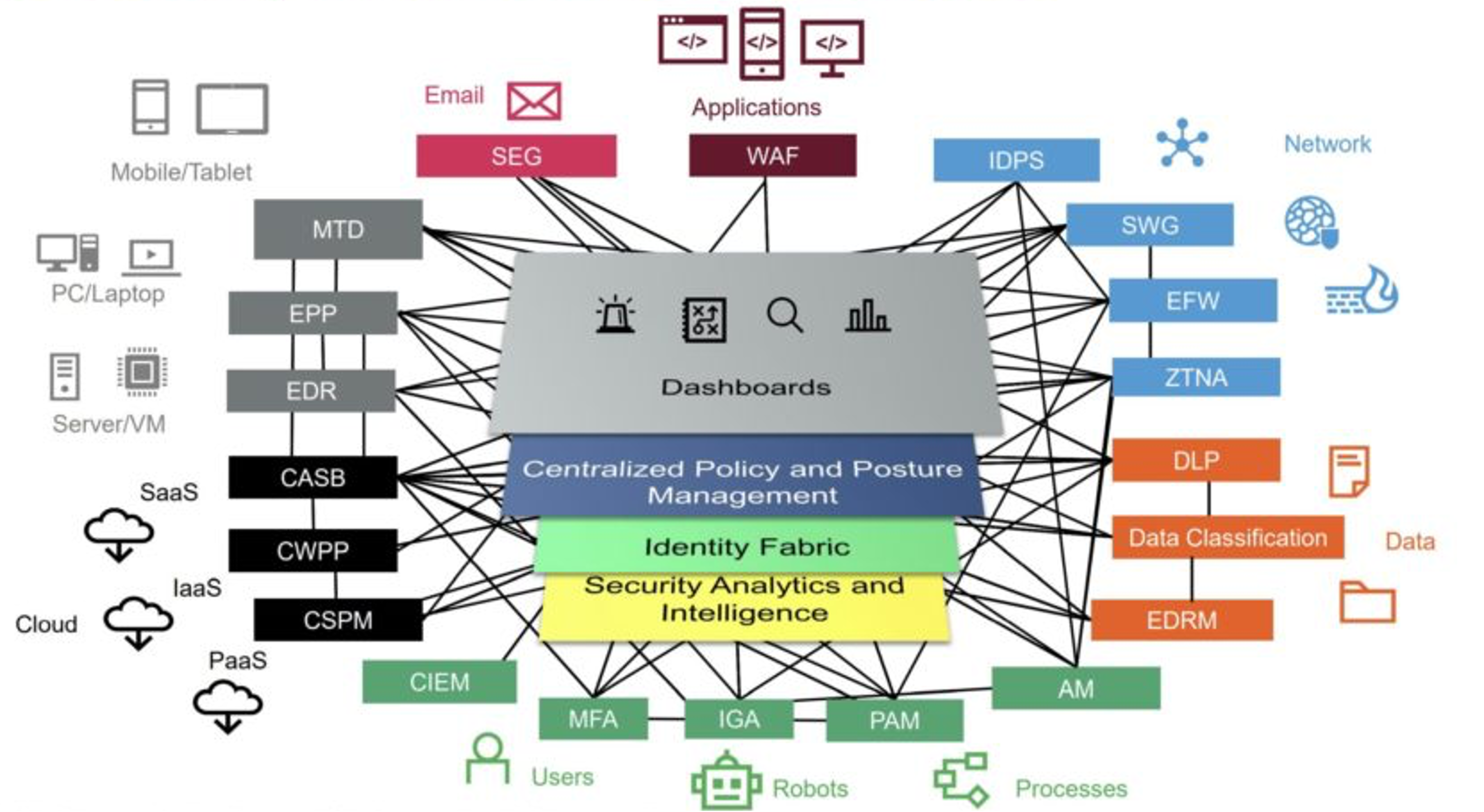
Source: Gartner
Devices & Servers
Cloud
Users, Robots & Processes
Data
Network
Applications
WAF
Web Application Firewall
Attacks on applications can be blocked with the right WAF solution in place. Applications contain valuable data, making them a prime target for attacks such as cross-site scripting, SQL injection, cookie poisoning, among others.
SEG
Secure Email Gateway
All emails, incoming and outgoing, pass through a SEG. The SEG prevents unwanted emails such as spam, phishing, malware and fraudulent content from being received. It also analyses outgoing emails to prevent sensitive data from the leaving an organisation, encrypting data where applicable.
Interested in the solutions mentioned above?
Complete the form and we will be in touch