Network-based security integration with Palo Alto Networks and Arista Networks provides dynamic automated deployment, deep visibility, and robust security for both physical and virtual workloads
Data centers have increasingly virtualized and partitioned their networks, becoming more dynamic while accommodating on-the-fly deployment of new applications within shared private, public, and hybrid clouds. Furthermore, hackers are finding new ways to breach the data center with an influx of new vulnerabilities and threats that need to be protected. Enterprises are faced with the complexity of implementing an agile security architecture to address a hybrid environment of microservices, virtual workloads, and legacy applications to protect critical assets from modern threats.
Arista Macro-Segmentation Service
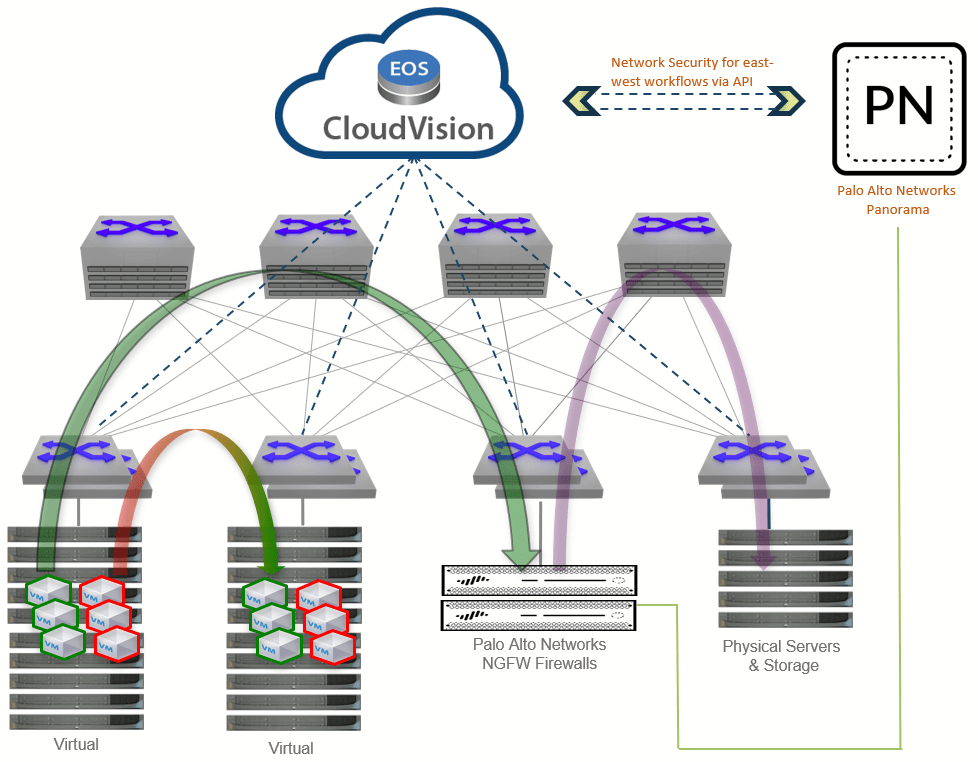
Arista Networks Macro-Segmentation Service (MSS) capability for CloudVision allows a variety of platforms, such as next-generation firewalls, to be deployed automatically for specific workloads and workflows across any network topology, including Layer 2, Layer 3, and overlay network virtualization frameworks.
Macro-Segmentation Service is a capability within Arista CloudVision that addresses a growing gap in security deployment for hybrid data centers. It extends the concept of fine-grained intra-hypervisor security for VMs to the rest of the data center by enabling dynamic insertion of services for physical devices and non-virtualized devices. It is specifically aimed at physical-to-physical (so-called P-to-P) and physical-to-virtual (P-to-V) workloads, with complete flexibility on the placement of service devices and workloads.
Palo Alto Networks und Arista MSS
By integrating with native APIs provided by the leading Palo Alto Networks Next-Generation Firewalls in the data center (PA-3200 Series, PA-5200 Series, and PA-7000 Series) and Panorama – native APIs that already exist – Arista Macro-Segmentation Service learns the security policies, identifying the workloads the firewall needs to inspect the traffic and take action. Upon identification, MSS can now steer interesting traffic to the firewall, thus enabling a logical topology of the firewall in the path of workload flows.
The automation capabilities of Arista Macro-Segmentation security operate in real-time, and without any need for a network operator to engage the security administrator (or vice versa). Furthermore, there is no need for the network to be architected in a manner specific to a particular workload. This flexibility is crucial to the successful deployment of security in an enterprise private or hybrid cloud. With this new integration, security policies in Palo Alto Networks Next-Generation Firewalls an be instantiated form the central point and implemented across the network topology.
Possible use cases include:
Intelligent Inspection of East-West Traffic on Demand
Using the API plane, Arista Cloud Vision obtains the interesting rules from Palo Alto Networks Panorama, a centralized network security management console, and programs the Arista switches to steer intercepted east-west workload traffic to the Palo Alto Networks Next-Generation Firewall for robust traffic and content inspection as well as policy enforcement. Security admin can now have the flexibility to add or remove policies to monitor traffic between workloads on demand, and they can profile traffic to detect malware of DoS attacks from within the enterprise proactively.
Complete Flexibility on Devices Across the Network
Service devices such as the Palo Alto Networks Next-Generation Firewall can be connected anywhere in the network on any switch. This allows larger data centers to centralize their security devices in a service rack and logically insert them in the path between any workloads on demand or based on a firewall policy. There are no restrictions or limitations on where the service devices are physically attached within the fabric. Palo Alto Networks firewalls are discovered via LLDP. Likewise, devices to which services are targeted can be located anywhere in the networks with no restrictions or limitations on physical placement.
Intelligent Security Policies Offload to Network
Arista’s Macro-Segmentation Service does not try to «own security policy». In addition to redirection of interesting traffic to the firewall, security administrators can define rules within Palo Alto Networks Panorama, marking them as offload policy. The offload tag, when applied to a policy, identifies a 5-tuple and the action (permit/deny). This allows the firewall admin to offload predictable traffic, which need not be inspected, or disallow traffic between any pair of segments. This new offload function enables the firewall admin to have a central control point and expand the security domain. In addition, this allows the firewall to provide high-performance, deep packet inspection and intrusion prevention services.
Key benefits of the integration include:
- Dynamic service insertion
- Complete flexibility on locality of devices
- No new frame formats or protocol required
- Software-driven: leverages automation for network security integration
For more information about the Arista Networks and Palo Alto Networks portfolios and their integration, please contact your local Exclusive Networks Account Manager.