
Securing Your Business in 2025: The Power of F5 Distributed Cloud
As we approach 2025, the cybersecurity industry continues to evolve at an unprecedented pace. […]

As we approach 2025, the cybersecurity industry continues to evolve at an unprecedented pace. […]

The Palo Alto Networks Security Lifecycle Review (SLR) is an online tool that summarizes […]

Attackers are targeting user identities with increasingly sophisticated phishing techniques, as compromised credentials make […]

Networking and security convergence are increasingly important when looking at how to manage customers’ […]

Are you a system integrator seeking better ways to manage customers’ network infrastructure and […]

Even before the 2020 pandemic, it was becoming clear work is no longer a […]

5G is rapidly entering our lives and all areas of application. Over the next […]

Automated, on-demand scanning and threat intelligence sharing are just a few simple functions that […]

Since the time of VMware and HyperV on-prem IaaS services, it was becoming apparent […]

Containers and Kubernetes used to be complicated. Developers and IT operations avoided it as […]

It is clear that the modern data center is software driven, and we can […]
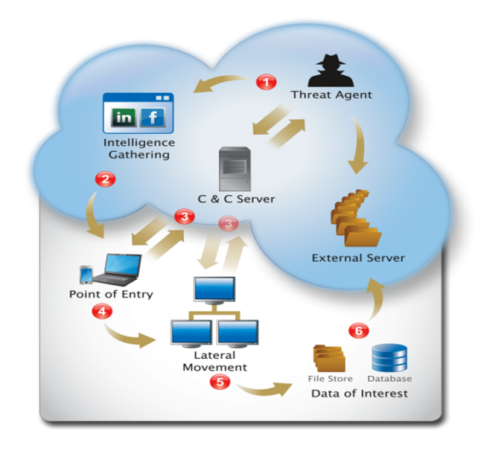
To discover insider and outside malicious actors and advanced persistent threats within networks, organizations […]

Given the subject matter and content of the client meetings I have attended lately, […]

Svi smo čuli za OfficeScan, a mnogi od vas ga i koriste. Kada govorimo […]

Latest research examines real-world vulnerability assessment practices at 2,100 organizations to understand how defenders […]

Modern authentication scenarios for web access usually include federated identities with claims-based authentication (SAML, […]

Given the number of video conferencing solutions available, it can sometimes be daunting to […]

You just bought a new car, and it’s already infected with malware. You wouldn’t […]

Tenable Black December: 10% Off Nessus Products Vulnerability scanning is an organized approach to […]

Let’s face it. There is no peace time. DDoS attacks are nothing new in […]

IP addresses are typically a very important part of any network and managing them […]
Seeing is believing. While that is generally the case, it only applies when other […]

PSD2 and open banking are forcing the banking sector to rethink their digital banking […]

In our first article we have touched upon the nature of F5 BIG-IP Cloud […]

This is the first part of our F5 BIG-IP Cloud Edition series blog; in […]

In a world where new cyber-attacks are created and appear each and every day, […]

Google takes security and safety of its users very seriously, embarking on a years-old […]
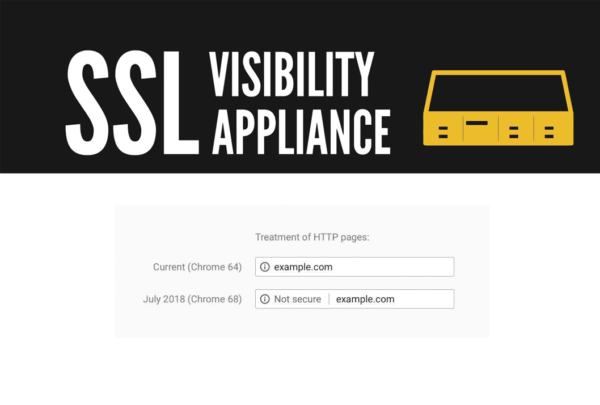
This week, Google released Chrome version 68, currently, by far the most popular web […]
Many modern jobs don’t require you to be physically present at the office. You […]

What do users consider important when it comes to apps? First of all, their […]
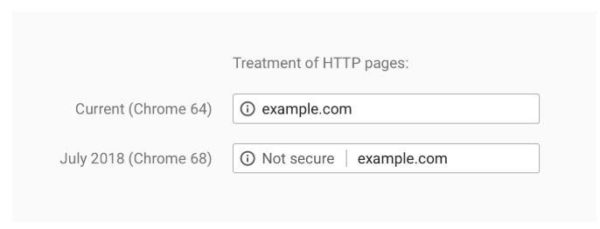
Version 68 of the Google Chrome browser, announced for the beginning of July 2018, […]

Polycom EagleEye Director II introduced last year brings even more big news with the latest upgrade. […]

With its new EagleEye MSR camera, Polycom Trio finally scaled up from small huddle […]

Do you use Microsoft Skype for Business as your communications platform for videoconferencing with […]

In last year’s survey on top new technologies for information security, Gartner has highlighted […]

The inaugural Gartner report for Cloud Access Security Broker products positioned Symantec CloudSOC platform […]

[vc_row][vc_column][vc_column_text] There is little time left until the deadline for full implementation of the […]

After the release of the latest version of OfficeScan XG – which comes with XGen functionality for heuristic […]

One of the products that was among the first to be integrated into the […]

In our last post, we presented BIG-IP APM product and some of its functionalities. […]

F5 BIG-IP Access Policy Manager is flexible security solution with high performance which enables […]

With the emergence of the WannaCry epidemic in May and Petya worm attack in […]
SSL is a set of cryptographic protocols that protect data during transmission. Although nearly […]

After the Wannacry ransomware attack last month, a new ransomware attack is underway that […]

The story of WannaCry ransomware and critical vulnerability of Windows operating systems occupied the […]

What is really new about the massive Wannacry ransomware attack? And how does it […]

Security professionals and consultants have recently taken greater interest in a specific functionality of […]

Wireshark is a free and open source software utility for analyzing network traffic. IT […]

Our previous article outlined powerful features of Symantec Elastica CloudSOC product portfolio aimed at providing full […]
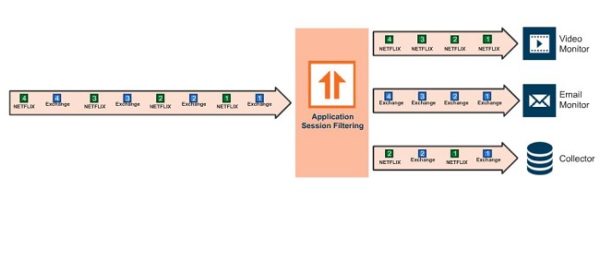
Gigamon Visibility Fabric is no longer a novelty in the world of network traffic […]

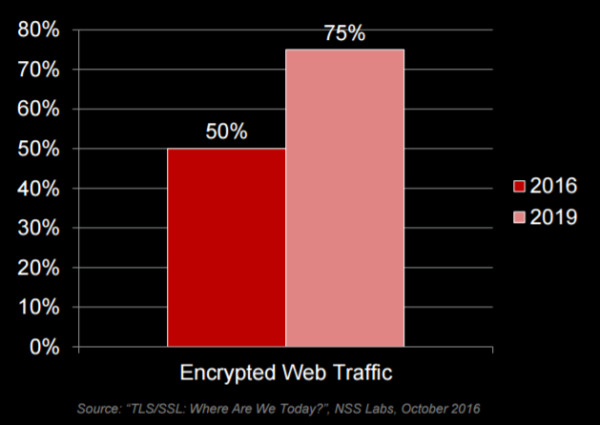
HTTP is becoming the past. More accurately, non-encrypted HTTP is becoming the past: SSL […]

The need for data encryption is constantly increasing due to regulatory requirements on data […]

In early 2017, Google initiated the first phase of its plan to display all […]